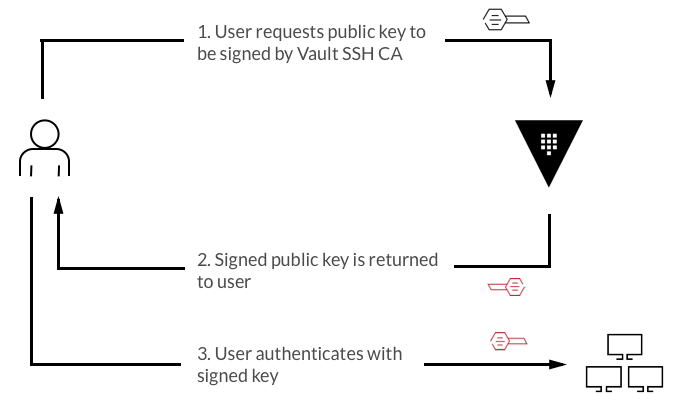
Vault를 사용하여 SSH 인증을 관리하는 방법(ssh authentication)
테스트 환경
| 호스트 이름 | 아이피 | 역할 | 운영체제 | 비고 |
| node141 | 192.168.0.141 | vault server | ubuntu 24.04 | |
| node142 | 192.168.0.142 | ssh server | ubuntu 22.04 | |
| node143 | 192.168.0.143 | ssh client | ubuntu 22.04 |
Vault 데이터 디렉터리 초기화 및 서버 재시작
sudo systemctl stop vault
sudo rm -rf /opt/vault---
GPG 키와 저장소 추가
wget -O- https://apt.releases.hashicorp.com/gpg \
| sudo gpg --dearmor --yes -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" \
| sudo tee /etc/apt/sources.list.d/hashicorp.listVault 설치
sudo apt update
sudo apt install -y vault
vault versionVault 설정 파일 구성
sudo tee /etc/vault.d/vault.hcl > /dev/null <<EOF
ui = true
storage "file" {
path = "/opt/vault/data"
}
# HTTP listener
listener "tcp" {
address = "0.0.0.0:8200"
tls_disable = 1
}
EOFVault 서비스 시작 및 확인
sudo systemctl enable --now vault
sudo systemctl restart vault
sudo systemctl status vaultVault 서비스 로그 확인
sudo journalctl -xeu vault
sudo journalctl -u vault -b---
sudo mkdir -pv /opt/vault/data
sudo chown -R vault.vault /opt/vault
sudo systemctl start vaultsudo systemctl status vaultVault 초기화 및 언실
환경변수 설정
echo "export VAULT_ADDR=http://127.0.0.1:8200" >> ~/.bashrcsource ~/.bashrcseal 상태 확인
vault statusVault 초기화(Initialize Vault)
vault operator init -key-shares=1 -key-threshold=1 | tee vault-init-$(date +"%Y%m%d-%H%M%S").txtVault UI 접속
http://192.168.0.141:8200unseal 및 로그인
vault operator unseal {Unseal Key}
vault operator unseal yR+JSTCt2nXZI0axjiu3kQp1TPSP2XpDMGv1+WbYw/8=vault login {Initial Root Token}
vault login hvs.OXgyLZfl8wnutNnda1FK3Cd2토큰(token)에 대한 정보 표시
vault token lookupseal 및 HA 상태 출력
vault statusSyslog를 통한 Vault Audit 로깅 활성화
vault audit enable syslog[Vault Server]
SSH Client-Signer Secrets Engine 활성화 및 CA 키 생성
SSH Client-Signer Secrets Engine 활성화
vault secrets enable -path=ssh-client-signer sshCA(인증 기관) 키 생성
vault write ssh-client-signer/config/ca generate_signing_key=trueCA(인증 기관) 키 출력
vault read -field=public_key ssh-client-signer/config/ca > /etc/ssh/trusted-user-ca-keys.pemcat /etc/ssh/trusted-user-ca-keys.pemSSH 인증 역할 설정(my-role)
서명된 인증서를 통해 인증 가능한 사용자를 제한하고 기본 사용자 및 인증서 TTL(Time To Live)을 설정합니다.
vault write ssh-client-signer/roles/my-role -<<"EOH"
{
"allow_user_certificates": true,
"allowed_users": "*",
"valid_principals": "vuser1",
"default_extensions": [
{
"permit-pty": ""
}
],
"key_type": "ca",
"default_user": "vuser1",
"ttl": "30m0s"
}
EOHrole 정보 확인
vault read ssh-client-signer/roles/my-role[Target : SSH Server]
각 호스트에 CA의 공개 키 추가
SSH 서버 설정 (CA 키 설정)
Vault에서 생성한 CA 키를 SSH 서버에서 신뢰하도록 설정합니다.
trusted-user-ca-keys.pem(/etc/ssh/trusted-user-ca-keys.pem) 저장
curl -s http://192.168.0.141:8200/v1/ssh-client-signer/public_key -o /etc/ssh/trusted-user-ca-keys.pemcat /etc/ssh/trusted-user-ca-keys.pemssh(sshd) 설정(/etc/ssh/sshd_config)
echo 'TrustedUserCAKeys /etc/ssh/trusted-user-ca-keys.pem' >> /etc/ssh/sshd_configecho "PubkeyAcceptedKeyTypes=+ssh-rsa,ssh-rsa-cert-v01@openssh.com" >> /etc/ssh/sshd_configssh(sshd) 설정 확인
cat /etc/ssh/sshd_config | egrep 'TrustedUserCAKeys|PubkeyAcceptedKeyTypes'ssh(sshd) 재기동
sshd -tsystemctl restart sshd[Client]
Vault 설치
바이너리 파일로 vault를 설치합니다.
apt install -y unzip
curl -fsSL https://releases.hashicorp.com/vault/1.18.0/vault_1.18.0_linux_amd64.zip -o vault_1.18.0_linux_amd64.zip
unzip vault_1.18.0_linux_amd64.zip
mv vault /usr/local/bin/
vault version
rm -f LICENSE.txt vault_1.18.0_linux_amd64.zip클라이언트 측 환경 변수 설정
Vault 주소와 토큰을 설정하여 SSH 클라이언트에서 Vault와 쉽게 상호작용할 수 있게 합니다.
- VAULT_TOKEN = ssh client에서 생성한 token value 입력(require-ssh-sign token)
echo 'export VAULT_ADDR=http://192.168.0.141:8200' >> ~/.bashrcecho 'export VAULT_TOKEN="hvs.OXgyLZfl8wnutNnda1FK3Cd2"' >> ~/.bashrcsource ~/.bashrcenv | grep VAULT클라이언트 측 SSH 키 생성 및 서명
클라이언트에서 SSH 키를 생성하고 Vault에서 서명된 인증서를 생성하여 SSH 접속에 사용합니다.
SSH 키 생성
ssh-keygen -t rsa -C "vuser1@vault"Vault에서 SSH 키 서명 요청
vault write -field=signed_key ssh-client-signer/sign/my-role public_key=@$HOME/.ssh/id_rsa.pub > ~/.ssh/signed-cert.pub파일 권한 설정
chmod 644 ~/.ssh/signed-cert.pub인증서 확인
cat ~/.ssh/signed-cert.pub서명된 인증서 확인
ssh-keygen -Lf ~/.ssh/signed-cert.pubSSH 서버로 접속
ssh -i ~/.ssh/signed-cert.pub -i ~/.ssh/id_rsa vuser1@192.168.0.142
참고URL
- Hashicorp Releases : Vault Binary download(https://releases.hashicorp.com)
- HashiCorp Vault를 이용한 SSH 공개키 인증 : https://ikcoo.tistory.com/251
- Signed SSH Certificates : https://developer.hashicorp.com/vault/docs/secrets/ssh/signed-ssh-certificates
- client key signing : https://developer.hashicorp.com/vault/docs/secrets/ssh/signed-ssh-certificates#client-key-signing
- host key signing : https://developer.hashicorp.com/vault/docs/secrets/ssh/signed-ssh-certificates#host-key-signing
- 複雑なポリシーを適切に管理する、HashiCorp Vault SSH CA動的シークレットエンジンとSentinel : https://www.lac.co.jp/lacwatch/service/20200811_002237.html
- Managing Developer Access with Vault SSH : https://pacewisdom.com/blog/managing-developer-access-with-vault-ssh/
'리눅스' 카테고리의 다른 글
| [draft] Consul 클러스터를 구성하는 방법 (0) | 2023.01.26 |
|---|---|
| [draft] 우분투에 Consul을 설치하고 설정하는 방법 (0) | 2023.01.26 |
| [draft] 리눅스에서 파일 디스크립터를 확인하고 설정하는 방법 (0) | 2023.01.25 |
| docker nettools (0) | 2023.01.25 |
| [리눅스] centos에 hashicorp vault를 설치하는 방법(installing vault) (0) | 2023.01.25 |



